Microsoft + Creto
Unified Identity & Access Across the Microsoft Ecosystem
From Azure Active Directory to Microsoft Entra, Creto helps enterprises maximize the security and operational potential of their Microsoft identity stack—seamlessly integrating policy, access governance, and threat protection under one strategy.

The Challenge
While Microsoft offers powerful identity tools, enterprises often struggle to:
- Fragmented identity experiences across Entra, AD, and third-party apps
- Limited contextual policy enforcement beyond Microsoft 365
- Gaps in threat detection and lateral movement inside the identity layer
- Difficulty aligning with compliance frameworks across multiple geos

The Solution: Extend & Secure Microsoft Identity with Creto
Creto complements Microsoft’s native stack by layering zero trust, contextual access, and deep risk analytics across your infrastructure:
What you get with Creto + Microsoft:
- Adaptive access policies across hybrid AD & cloud apps
- Unified audit trail for all user, device, and privilege activity
- Identity-based threat signals integrated with Microsoft Defender
- Streamlined provisioning/deprovisioning with Entra workflows
- Compliance-ready posture for GDPR, ISO, HIPAA, NIST
One multinational manufacturer used Creto + Microsoft to roll out a global zero-trust model—spanning 11,000+ employees and 50+ cloud apps—without overhauling their existing Azure AD infrastructure.
Where Microsoft Meets Creto
Maximize the impact of your Microsoft security stack by integrating it with Creto’s intelligent identity orchestration. From hybrid environments to modern collaboration tools, Creto strengthens and extends your Microsoft ecosystem across every user touchpoint.
1
Integrating third-party apps with Entra policies & MFA
Extend Microsoft Entra’s security policies—including multifactor authentication—to non-Microsoft and legacy applications, ensuring consistent protection across your digital ecosystem.
2
Managing guest access securely in Microsoft Teams/SharePoint
Gain granular control over external users by applying context-aware rules and expiration-based access to collaboration tools like Teams, SharePoint, and OneDrive.
3
Monitoring identity-based risks using Defender + Creto alerts
Combine Microsoft Defender’s insights with Creto’s behavioral analytics to detect anomalies, lateral movement, and privilege escalation—before they lead to breaches.
4
Automating access reviews for privileged AD accounts
Ensure continuous compliance by triggering automated, scheduled access certifications and reviews for high-risk accounts within Active Directory and hybrid environments.
5
Enforcing Just-in-Time (JIT) access to critical Microsoft resources
Reduce standing privileges by granting temporary access to sensitive resources only when needed—automatically revoked when tasks are completed or time expires.
6
Applying conditional access policies to legacy systems via hybrid AD
Extend Microsoft’s conditional access logic to on-premises and legacy applications through hybrid Active Directory, ensuring identity policies apply uniformly across environments.
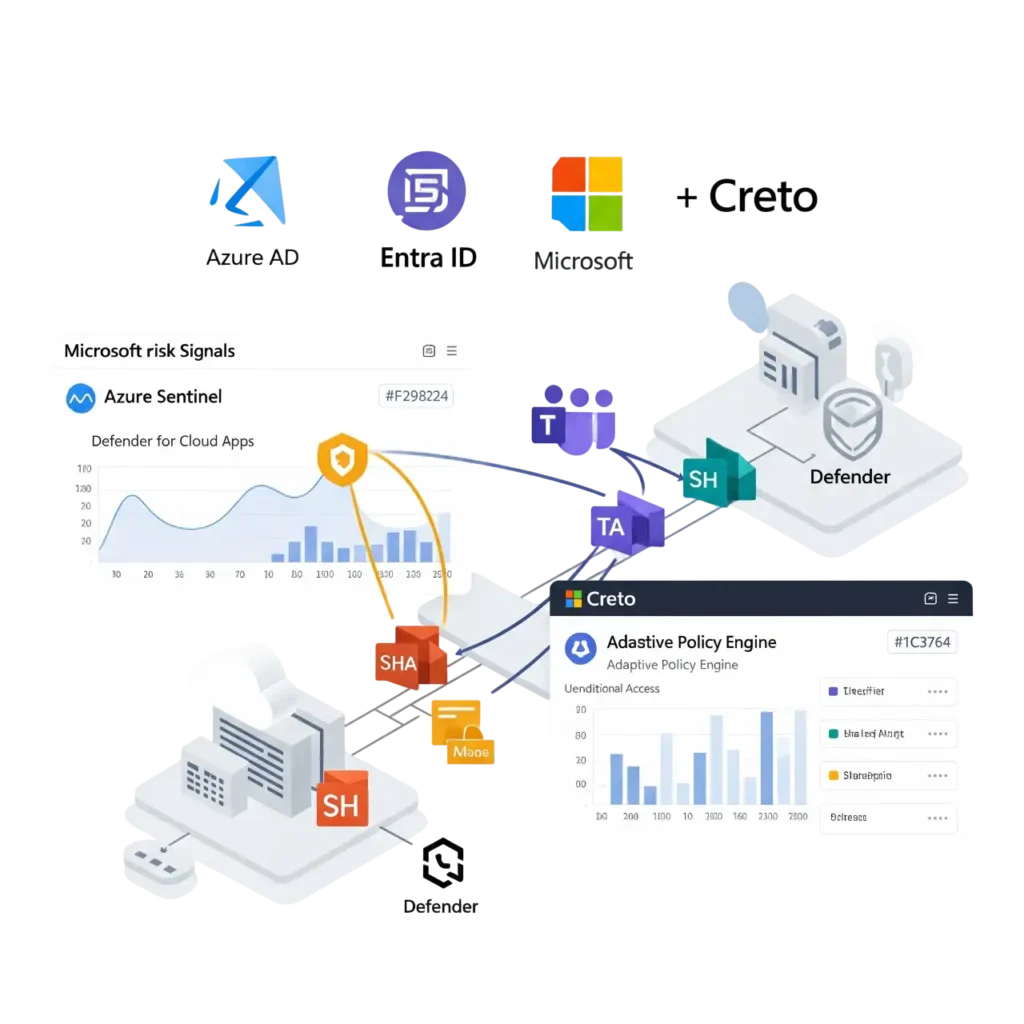
The Integration: Adaptive, Unified, Microsoft-Ready
Our deep integration with Microsoft empowers you to unify:
- Unified Access Control across Azure AD, Entra, and third-party apps
- Adaptive Risk-Based Authentication powered by real-time data signals
- Automated Lifecycle Management for Teams, SharePoint, and sensitive content
How it works:
- Creto integrates with Microsoft Entra, Azure AD, Defender, and Microsoft Graph.
- Creto enforces dynamic, context-aware access policies based on user behavior and risk.
- All activity is logged, ensuring compliance and visibility for audits.
Modern identity signals meet Microsoft’s enterprise backbone.
Strategic Outcomes
Outcome
- Enhanced Security Posture
- Improved Compliance
- Cost Savings
- Better UX
Value Delivered
- Detect and respond to threats faster using unified identity signals.
- Simplify audits and demonstrate policy enforcement across environments.
- Maximize existing Microsoft investments and reduce tool sprawl.
- Maintain seamless user experience while enforcing advanced access controls.
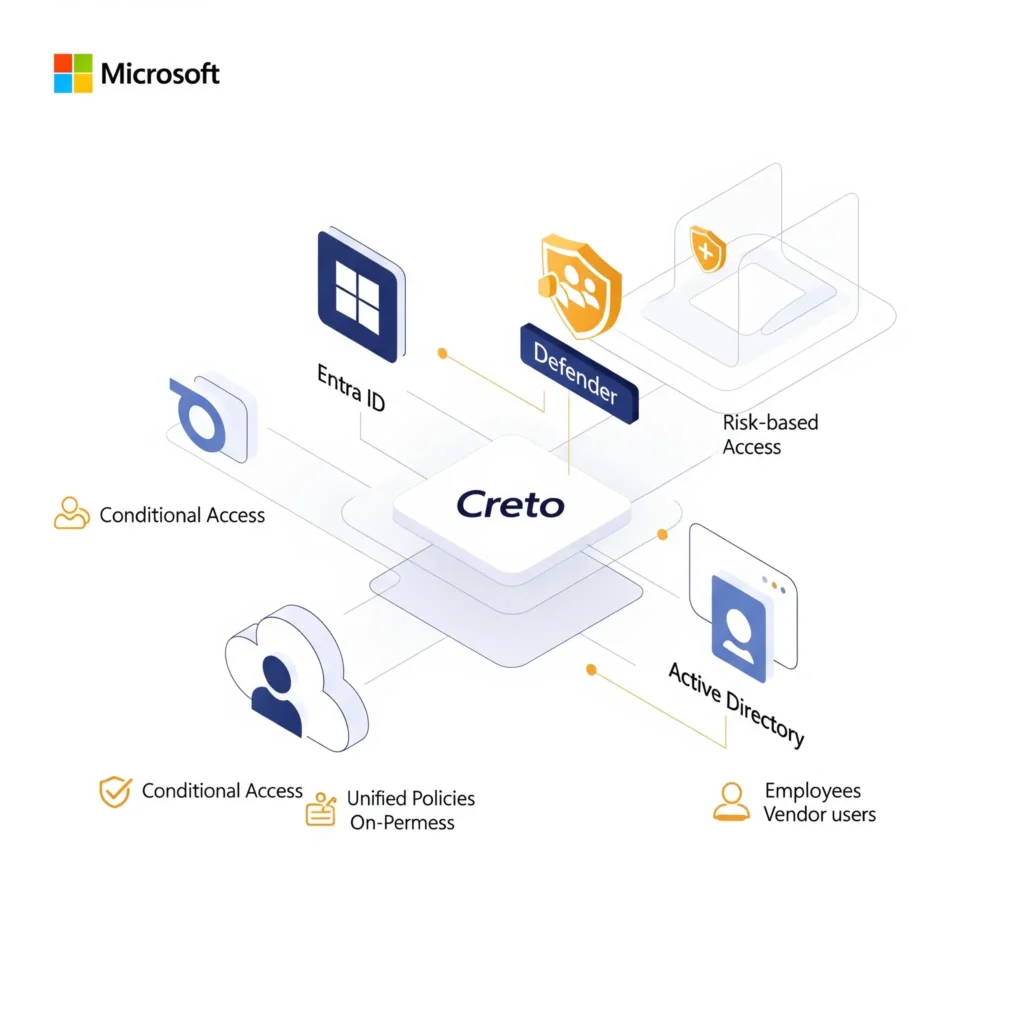
Why Extend Microsoft with Creto?
Creto helps enterprises do more with Microsoft’s security investments—by filling critical identity gaps. Whether you’re bridging hybrid environments, modernizing access for legacy apps, or enforcing finer-grained controls, Creto complements Microsoft with:
- Cross-platform conditional access enforcement
- Unified identity policy orchestration across SaaS, on-prem, and hybrid
- Behavior-based risk scoring for smarter access decisions
- Seamless UX for employees, vendors, and guests
Key Identity Enhancements
Hybrid Conditional Access
Extend Azure AD’s Conditional Access to legacy apps via Creto’s policy engine.
Privileged Access Management (PAM)
Add just-in-time access, approval workflows, and session monitoring to Microsoft AD.
Behavioral Analytics
Use AI-based behavioral risk scoring to refine Microsoft identity decisions.
Guest Access Governance
Automate access expiration, review cycles, and audit trails for Teams & SharePoint guests.
Risk-Based Authentication
Dynamically escalate MFA or block access based on device posture, location, or anomalies.
Unified Audit & Reporting
Consolidate logs across Entra, Teams, SharePoint, and Defender into Creto’s compliance dashboard.
Microsoft provides the foundation. Creto makes it dynamic, risk-aware, and unified.
While Microsoft secures access at scale, Creto enhances visibility, adaptability, and governance across hybrid and multi-cloud environments.
Related Microsoft Solutions
Explore how Creto works with key Microsoft use cases to secure, scale, and simplify enterprise identity and productivity
Workforce Identity
Discover how Creto enhances Microsoft Entra to streamline workforce onboarding, adaptive access, and lifecycle automation.
Office Productivity
Learn how Creto aligns identity with Microsoft 365 to secure collaboration and reduce friction across apps and devices.
Data Governance
Enforce fine-grained access and conditional controls on Microsoft environments to meet compliance and minimize insider risks.
Gen AI
Apply governance and role-aware controls to Microsoft Copilot and other AI tools, so only the right users get smart access to sensitive data.